
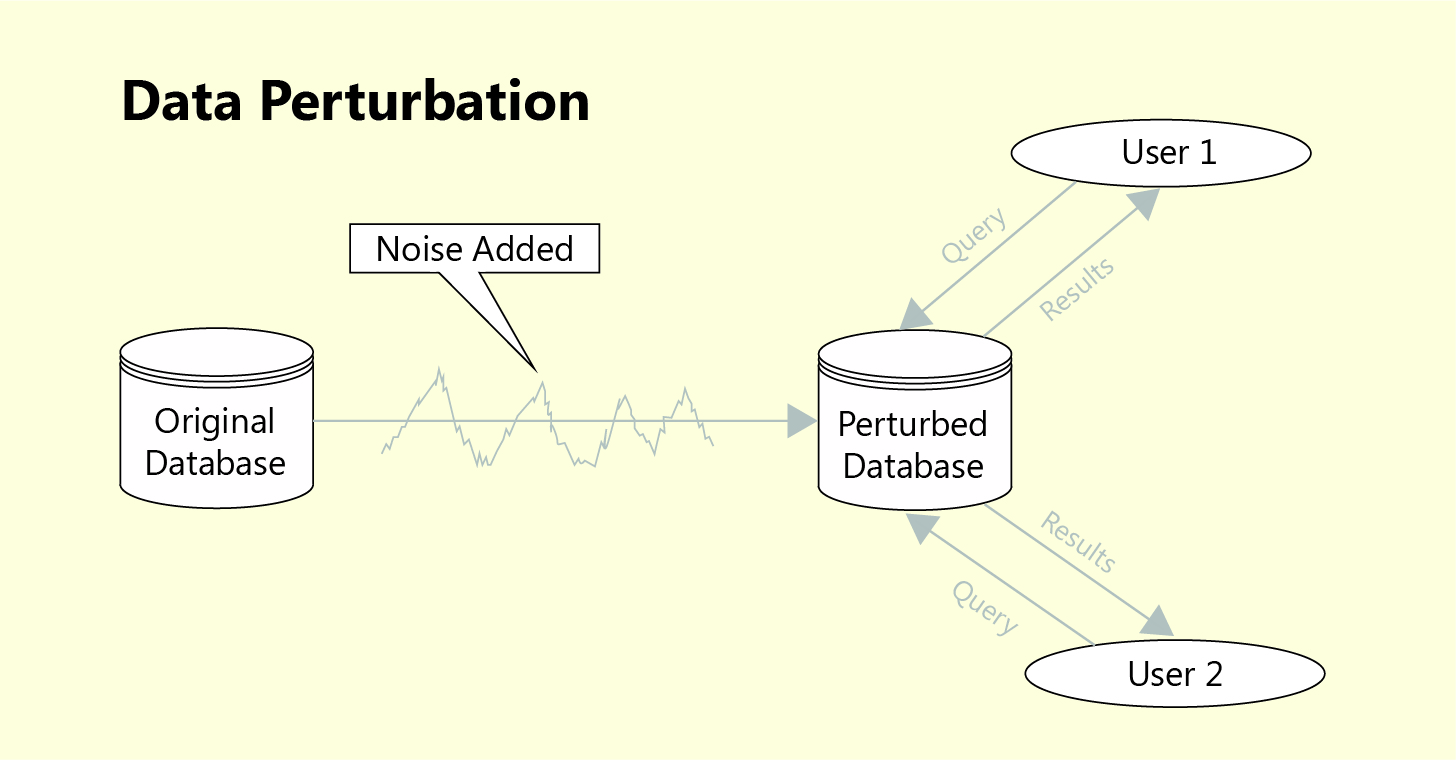
Data perturbation schemes to support multi-level privacy-preserving... | Download Scientific Diagram

Mathematics | Free Full-Text | Evaluating the Privacy and Utility of Time-Series Data Perturbation Algorithms

Privacy preserving data mining through the time-series data perturbation. | Download Scientific Diagram

Data Mining: Random Swapping based Data Perturbation Technique for Privacy Preserving in Data Mining | Semantic Scholar

Improved perturbation technique privacy‐preserving rotation‐based condensation algorithm for privacy preserving in big data stream using Internet of Things - N - 2020 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
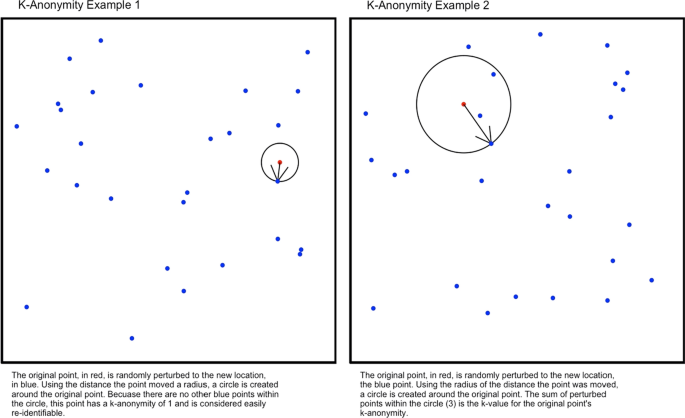
Measuring the impact of spatial perturbations on the relationship between data privacy and validity of descriptive statistics | International Journal of Health Geographics | Full Text
Combination of both data perturbation and function perturbation. The... | Download Scientific Diagram
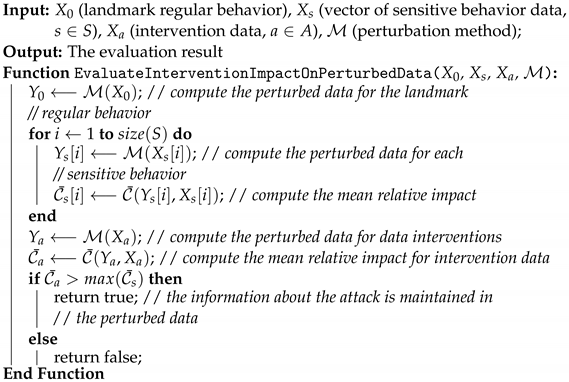
Mathematics | Free Full-Text | Evaluating the Privacy and Utility of Time-Series Data Perturbation Algorithms

Combination of both data perturbation and function perturbation. The... | Download Scientific Diagram

Multiplicative Data Perturbations. Outline Introduction Multiplicative data perturbations Rotation perturbation Geometric Data Perturbation Random. - ppt download

Design of Retrievable Data Perturbation Approach and TPA for Public Cloud Data Security | SpringerLink
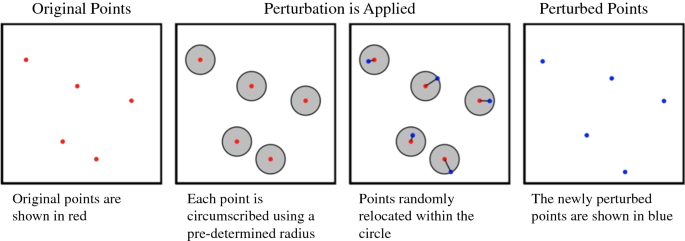









![Data Perturbation or Swapping [Series#2: I am Data!] Data Perturbation or Swapping [Series#2: I am Data!]](https://media.licdn.com/dms/image/C5612AQF6Q0C9n8wUIg/article-cover_image-shrink_600_2000/0/1648502191601?e=2147483647&v=beta&t=K1dK71j8v9DVuvq3mSqk2MAY13LZ56aiL1j61e0QgU0)
![PDF] Techniques of Data Perturbation for Privacy Preserving Data Mining | Semantic Scholar PDF] Techniques of Data Perturbation for Privacy Preserving Data Mining | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/060134f1210209c83bc24e18fc3582b7c4e7aa93/2-Figure1-1.png)
